The 2017 “WannaCry ransomware attack” infected about 230,000 computer systems around the world with organizations incurring a cost of about 4 billion dollars. Those organizations that heeded to the warning of Microsoft and applied the released patch to systems before the attack were not affected by the attack (“The WannaCry ransomware attack,” 2017). Like that incident, it is not uncommon that the news about data breaches, cyber-attacks, phishing, ransomware, denial of service, and identity theft is becoming more prevalent every day. Keeping up with and staying ahead of cyberattacks is challenging and costly. Organizations that invest in cybersecurity and risk prevention do so only to protect their assets and employees. What is missing here is the critical component of the risk prevention equation of the company’s vendors, trusted partners, or third parties. Because of that, an increasing number of security breaches are stemming from third parties who had access to organizations’ information. Cyber defenders, chief information officers, and information technology managers are concerned about the security risk posed by third parties, namely contractors, agents, distributors, vendors and suppliers (Beal, 2017, p. 153). Effectively and efficiently detecting threats and attacks continue to be among the most significant functional challenges. One of the avenues that organizations utilize to overcome those challenges is to hire more cybersecurity officers through increased budgets. Globally, the security budget increased by 4.9% in 2019 (Shust, 2015). As a result, the increase in the budget led to more security personnel, and layers of tools to old ad-hoc security architectures that only perpetuated the long-standing problem—many attacks continued to surmount, and the ability to prevent them becoming a far-fetching effort. It is alarming that no organization, including hospitals and health organizations, is immune to cyber-attacks.
A central concern in the process of managing and preventing cyber threats and attacks launched against hospitals is that of “third-party risk management.” Many outsourcers, suppliers, and vendors supply all electronic instruments, imaging, and medical devices, including implantable medical devices. The growing number of implantable medical devices have created security vulnerabilities due to technological advancements, and they further add to the already existing vulnerabilities in cyberspace (Baranchuk et al., 2018, p. 1284). Such security loopholes are clamoring for the attention of cybersecurity officials to curb unauthorized access to those devices. In the process to do so, those security officials forego the fact that third-party risk management is an essential need, and it must take into consideration specific procedures for dealing with third-party risk management.
According to the Ponemon Institute (2018), 78% of the hospitals in the United States faced at least one breach in 2018, and the future portrays a bleak picture. Nearly two-thirds expect to be breached in 2019. Table 1 shows the breakdown of attacks in healthcare institutions.
Table 1
Breakdown of attacks in healthcare
| Occurrences and causes | Motive and outcome |
| Rate of occurrence | 466 incidents; 304 data leak |
| Causes of breach | Various errors, “privilege misuse,” and “web applications” constituted 81%
|
| Actors | Internal (59%), External—vendors, and partners (46%), and
other parties (3%) |
| Reasons | Pecuniary (83%), Entertaining (6%), Handiness (3%),
Resentment (3%), and various parties (3%) |
| Data loss | Health (72%), Individual (34%), Identities (25%)”
|
Note: Adapted from “2019 Data Breach Investigations Report,” by Verizon, 2019, https://enterprise.verizon.com/resources/executivebriefs/2019-dbir-executive-brief.pdf
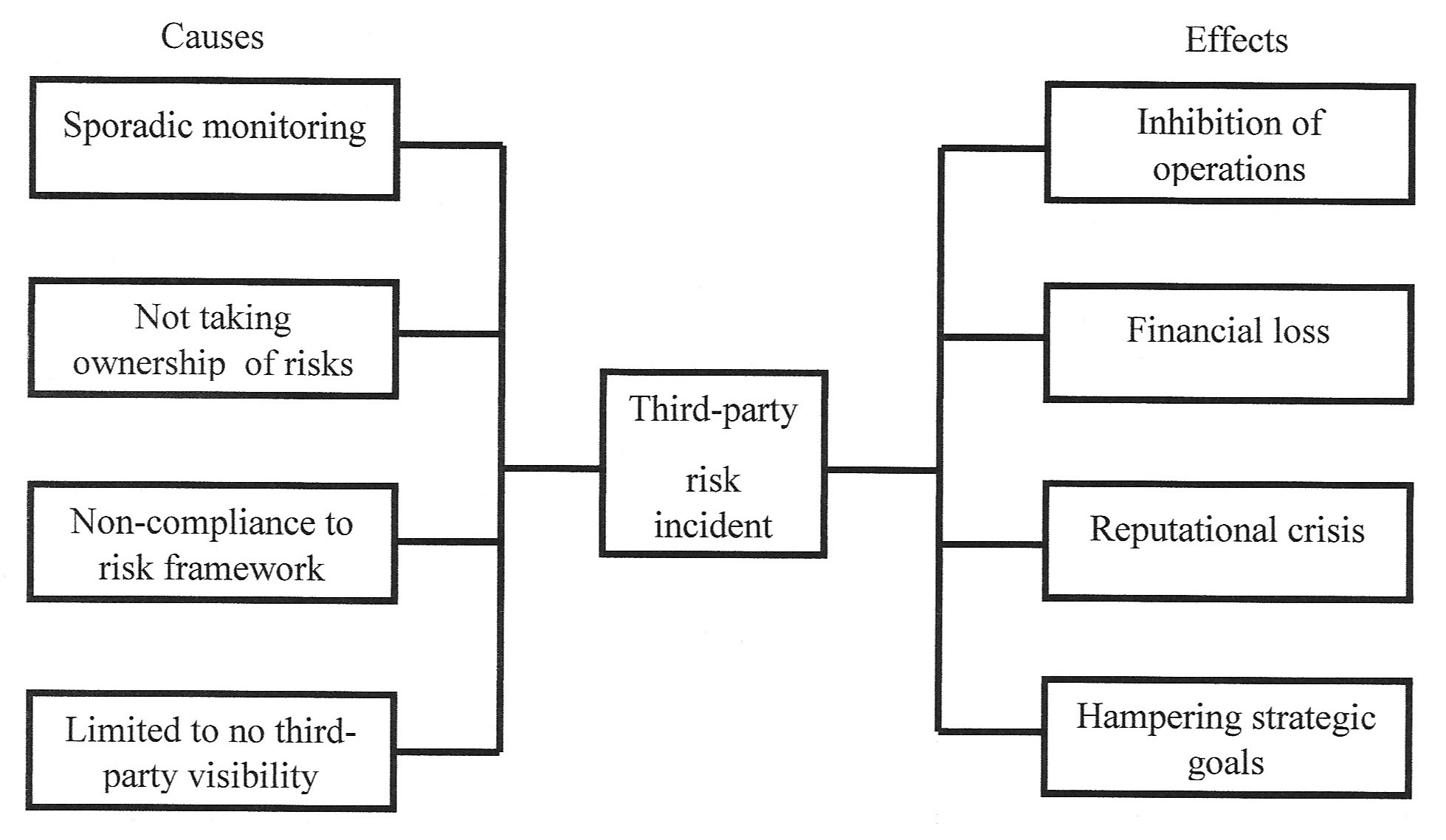
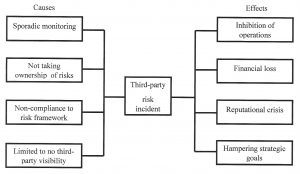
The report states that breaches in healthcare organizations were associated with vendors and employees within organizations who displayed erratic behavior (Verizon, 2019). Although the reality of breaches and attacks stem from various sources, risks due to vendor vulnerabilities pose destructive problems so as not to be neglected. For instance, if hospitals ignore the requirement of risk compliance for vendors, then the issues that emerge from such negligence might spawn reputation problems and open the door to increasing exposure to threat and risk compliance issues. Figure 1 shows several causes and outcomes as a result of third-party risks. The effects due to risk events can debilitate the normal operations of an organization.
Figure 1. Specific causes and effects of third-party risk incidents. Adapted from “Best practice vendor risk management in today’s interconnected world.” https://search-ebscohost-com.proxy1.ncu.edu/login.aspx?direct=true&db=bth&AN=126935164&site=eds-live. Retrieved July 31, 2019. Copyright 2019 by Journal of Business Continuity & Emergency Planning.
Even so, hospitals are facing an impossible challenge to provide the needed oversight of these third parties for minimizing risks. When hospitals either sporadically carry out that supervision or do not do that at all, those third parties can often become the breeding ground for cybercriminals to expand their attack surface—principle systems, connected devices, and supply chains. The rate at some of these suppliers and vendors grow both nationally and globally increases their structural complexities that hospitals tend to ignore because they mainly focus on their mission of providing service to patients and not waste time on anything else. Such negligence on the part of the hospitals results in totally avoiding the necessary review process that determines the standard for entering into business operations. At times, such a review process is considered to be burdensome and “an organizational drag” to avoid the risk assessment of those third parties. As a consequence, chief performance measures and internal audits such as “performance monitoring,” “risk monitoring,” and “compliance monitoring,” that are essential to a successful relationship end up neglected. Hence, hospitals have to make sure that vendors and suppliers adhere to security frameworks and conduct appropriately.
A typical structure such as the “National Institute for Standards and Technology (NIST)” offers standards and guidelines to manage cybersecurity-related risks. Based on that, a policy framework created by hospitals for their internal governance must encompass a third-party risk management strategy, procedures for a variety of functions and legal deliberations. After deploying needed structures, cybersecurity managers can resort to several tools that can aid them in monitoring data, facilitating workflow within different units of the organization, and keeping track of third-party operations (Lindros, 2017). For example, cybersecurity officials can use a “governance, risk management, and compliance (GRC)” platform that will enable them to capture a complete picture of performance management of third parties.
For implementing third-party risk programs, hospitals must overcome inconsistencies, lack of legal procedures, inconsistent standards, and unfortunate interdepartmental engagements. Moreover, plagued by rigid regulations and a strong motive to offer unprecedented patient care, hospitals tend to forget that security of the cyberspace operations should take priority along with managing third-party dealings. The following list of steps is presented to help with establishing a risk management program for third parties.
Eliminate blind spots. Every day hospitals produce voluminous patient, purchase, surgical, imaging, and maintenance data through spreadsheets and documents. Such an approach is susceptible to failure as they entomb the organization in the mountains of data that is problematic to manage, resulting in many blind spots in addition to demanding more time to “data management and reconciliation” instead of risk monitoring and prevention (Chapman, 2018). A better method would be to eliminate reliance on spreadsheets and emails and creating a central database for tracking third-party information.
Pave a distinct path to the destination. In the hospital scenario, the target is to develop and maintain an advanced cybersecurity system (Palm 2015). The road to reaching that terminus involves the discovery of security personnel, technology, a budget, and a reporting system that measures success.
Take stock of systems and assets. An inventory in the current context points to determine what information is on what network and hybrid infrastructure—cloud, virtual, and physical—complicates the whole course of action. As technology advances, the configuration of the systems and networks also change with the inclusion and exclusion of several units. Such constant change demands software updates and patches (Shuster, 2015). Keeping up with the vicissitudes of the hybrid environment requires proper technology management.
Automate vulnerability assessments. Taking stock of all assets do not reveal vulnerabilities and weaknesses (Cooper, 2019). When cyber defenders detect and store vulnerabilities using a severity scoring system, they can be of immense help in prioritizing the investigation of vulnerabilities and prevention efforts.
A Repository of third parties. Maintain a centralized storehouse of risk complaint third-party vendors, and suppliers, assessments of risks and mitigation. When done so, it establishes a consistent standard for the evaluation of third party relationships. Procurement managers can then move third-party contracts after they check them with pre-approved templates.
Technology review: Procure software that routinely analyzes and provides continuous automation and security monitoring. Furthermore, such tools also perform change detection, free up resources, automate processes, and aid in reducing human errors.
References
Beale, I. (2017). Best practice vendor risk management in today’s interconnected world. Journal of Business Continuity & Emergency Planning, 11(2), 151–162. Retrieved from https://search-ebscohost-com.proxy1.ncu.edu/login.aspx?direct=true&db=bth&AN=126935164&site=eds-live
Chapman, L. T. (2018). Building a Strong: Third-Party Risk Management Culture. RMA Journal, 100(7), 66–71. Retrieved from https://search-ebscohost-com.proxy1.ncu.edu/login.aspx?direct=true&db=bth&AN=128923916&site=eds-live
Cooper, B. (2019, February 19). Six steps for establishing a vendor risk management program [Blog post]. Retrieved from https://www.venminder.com/blog/6-steps-establishing-vendor-risk-management-program
Lindros, K. (2017, July 11). What is GRC, and why you need it? Retrieved from https://www.cio.com/article/3206607/what-is-grc-and-why-do-you-need-it.html
Myakovsky, M. (2016, August 18). Six steps for establishing a vendor risk management program [Blog post]. Retrieved from https://www.optiv.com/blog/six-steps-for-establishing-a-vendor-risk-management-program
Palm, S. (2015). Vendor Risk Management. RMA Journal, 97(5), 16–21. Retrieved from https://search-ebscohost-com.proxy1.ncu.edu/login.aspx?direct=true&db=bth&AN=100563857&site=eds-live
Ponemon Research Institute. (2016). Sixth Annual Benchmark Study on Privacy & Security of Healthcare Data. Retrieved from https://www.ponemon.org/local/upload/file/Sixth%20Annual%20Patient%20Privacy%20%26%20Data%20Security%20Report%20FINAL%206.pdf
Shust, J. (2015). Vendor management critical to supply chain continuity. Continuity Insights, Retrieved from http://search.proquest.com.proxy1.ncu.edu/docview/1668130838?accountid=28180
The WannaCry ransomware attack. (2017). Strategic Comments, 23(4), vii–ix. https://doi-org.proxy1.ncu.edu/10.1080/13567888.2017.1335101
Townsend, K. (2019, May 8). Verizon publishes 2019 data breach investigations report (DBIR). Retrieved from https://www.securityweek.com/verizon-publishes-2019-data-breach-investigations-report-dbir
Verizon. (2019, May 8). 2019 Data breach investigations report executive summary. Retrieved from https://enterprise.verizon.com/resources/executivebriefs/2019-dbir-executive-brief.pdf
Warren, P. D. (2014). Closing the Gaps in Third-party Risk Management. Internal Auditor, 71(1), 37–41. Retrieved from https://search-ebscohost-com.proxy1.ncu.edu/login.aspx?direct=true&db=bth&AN=100243396&site=eds-live