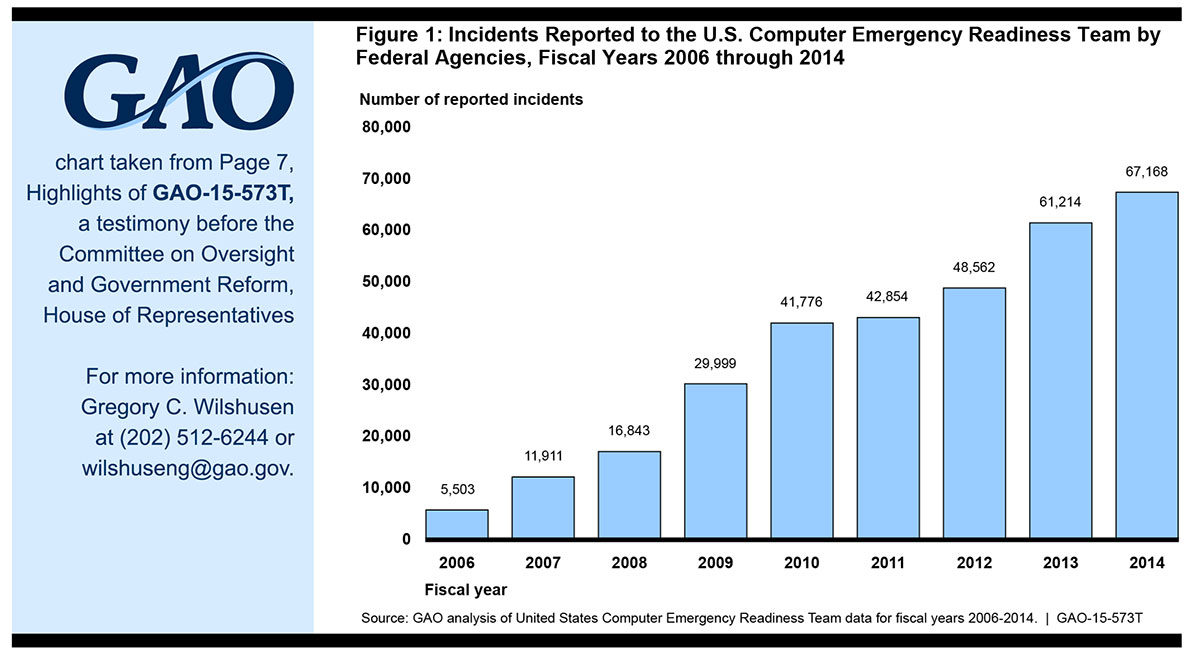
From cyberattacks to technology malfunctions, our private information is at risk every day. We have developed vast networks, security protocols, and automated processes to handle many of our daily tasks, and every industry–from military to finance to entertainment–has critical vulnerabilities revealed by attacks on data and functionality. We are facing serious gaps in both technology and the manpower to fix it.
Information Security = Job Security
Those with a degree or certification in information security have an excellent career outlook. According to the U.S. Bureau of Labor Statistics, the job outlook for Information Security Analysts is expected to grow 37% through 2022, well above the 11% projected growth rate for all occupations. Information security analysts also receive a median annual wage of $86,170, which is higher than the average $76,270 for all computer occupations. (source: Bureau of Labor Statistics, U.S. Dept. of Labor, Occupational Outlook Handbook, 2014-15 Ed., Information Security Analysts (visited July 13, 2015).
The path to these careers is found through both degree and certificate programs. Information security jobs are highly competitive, and require a comprehensive understanding of security and privacy throughout an organization’s technology network. IT security specialists set up and maintain their organization’s information security, from installing security software to responding to cyber attacks. And as cyber attacks become more sophisticated, approaches to information and network security must evolve in similar ways to counter the threat.
Growing a new cyber force
The Department of Defense outlined a new Cyber Strategy in April 2015, with a target of 133 Cyber Mission teams by 2018. The Mission Teams will have three primary goals: defending DoD networks, systems, and information; defending against cyberattacks; and providing cyber support to military plans.
We live in a time of growing cyber threats to U.S. interests. State and non-state actors threaten disruptive and destructive attacks against the United States and conduct cyber-enabled theft of intellectual property to undercut the United States’ technological and military advantage. …We must be dynamic, flexible, and agile in this work. We must anticipate emerging threats, identify new capabilities to build, and determine how to enhance our partnerships and planning. …By working together we will help protect and defend the United States and its interests in the digital age. (The DoD Cyber Strategy, PDF, April 2015)
To this end the Department of Defense, along with private sector and academic partners, hold annual Cyber Guard exercises that provide participants an opportunity to practice live cyber operations on a closed network against simulated adversaries. This approach blends industries with different backgrounds, to help share tactics in preparation for future cyberattacks on both government and the private sector.
Our area is becoming a hub for government cyber interests; the annual Cyber Guard exercise is growing rapidly each year, and the NSA and Defense Information Systems Agency have established a U.S. Cyber Command headquarters in Fort Meade, MD. From its inception in 2010, the Cyber Command staff has grown to just over 1,000; that number is expected to double over the next few years. The growth at Cyber Command has attracted the interest of technology companies in the area, including commercial tech and cybersecurity firms.
The White House has also recognized the need for more qualified candidates for technology jobs, especially positions in information technology and cybersecurity. Of the approximately 5 million available jobs in the U.S. today, almost a quarter are in IT fields such as software development and cybersecurity. Many of these jobs did not exist 10 years ago.
The average salary in a job that requires information technology (IT) skills … is 50 percent higher than the average private-sector American job. Helping more Americans train and connect to these jobs is a key element of the President’s middle-class economics agenda. …Employers across the United States are in critical need of talent with these skills. Many of these programs do not require a four-year degree. (“President Obama Launches New TechHire Initiative,” March 2015)
The TechHire initiative is focused on connecting more Americans to available technology jobs in order to keep the U.S. competitive in a global economy. TechHire is working with over 300 employer partners to recruit, train, and place applicants in over 120,000 open technology jobs. In addition, TechHire is seeking to expand training models to create more fast-track learning opportunities to meet the growing need for a tech workforce.
Cyber Virginia
In February 2014, Governor Terry McAuliffe signed Executive Order No. 8, launching the Virginia Cyber Security Commission, recognizing the economic benefit to creating new cyber jobs in Virginia. According to CompTIA’s 2015 Cyberstates (February 2015), almost 1 in 10 of Virginia’s private-sector workers are in tech industries, with an average wage of $105,000 per year. The tech industry drives 8.6% of Virginia’s economy, with over 275,000 tech industry jobs throughout the state.
The Cybersecurity 500 List for Q2 2015, published in April 2015 by Cybersecurity Ventures, lists 39 Virginia-based companies. Only California has more companies on the list, with 150. Massachusetts is behind Virginia with 35 companies. Steve Morgan, Founder and CEO of Cybersecurity Ventures, contemplates Virginia as a hotbed for cybersecurity:
Demand for vendor-furnished information security products and services by the U.S. federal government will increase from $7.8 billion in FY 2014 to $10.0 billion in 2019 … according to Deltek’s Federal Information Security Market Report (published Oct. 2014)…. When you consider these market-sizing estimates and projections, which align to the federal sector – and all of the federal agencies that are headquartered in Virginia – it explains a lot. (Virginia is for Cybersecurity, July 7, 2015)
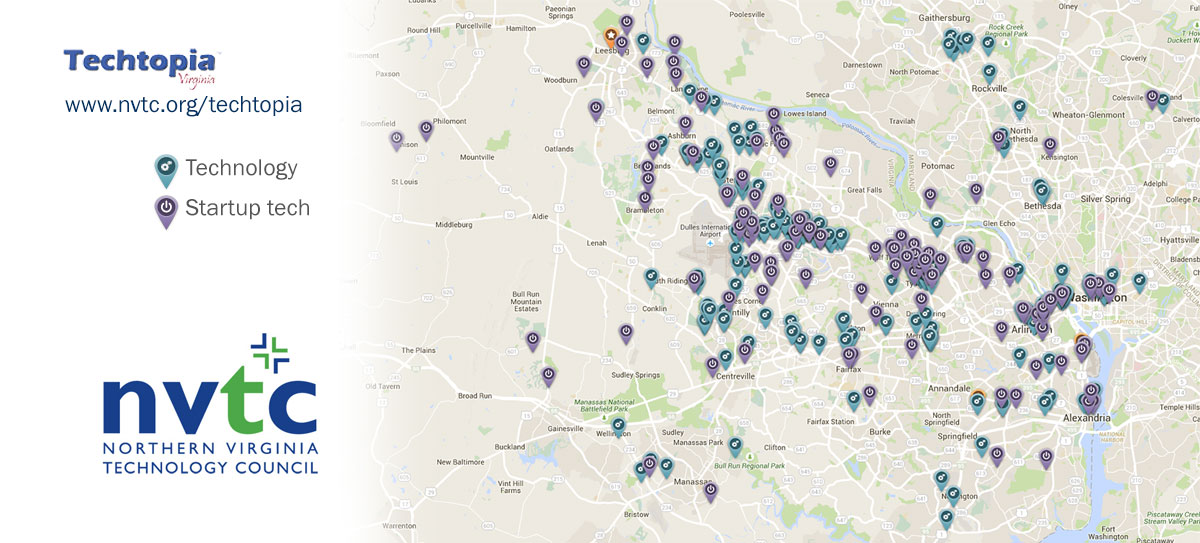
With all the companies in Virginia dedicated to advancing cybersecurity and new technologies for information networks, there is an accompanying need for a trained workforce to fill these positions. The “Techtopia” map below, provided by Northern Virginia Technology Council, shows the concentration of tech and cyber companies in Northern Virginia.
Become a cyber professional
In April I discussed the job outlook for cybersecurity professionals and NOVA’s Workforce Development Division dedication to addressing the skills gap here in Northern Virginia. To meet the growing need for Information and Cybersecurity professionals in the area, our Cyber Security certificate program includes entry-, mid-, and advanced-level certificates in Cyber Security. We have many IT and computer skills certificates available to IT professionals who are already working in Information Security, and provide customized training to organizations who need to advance skills of IT staff. For information on our cybersecurity certificate programs, call 703-948-3703.

Northern Virginia Community College’s Workforce Development Division is dedicated to improving Northern Virginia’s economic development and business landscape with a comprehensive variety of training options, including Professional Development, Certificate Programs, Enrichment Courses, Continuing Education, and Customized Training. Visit us online to learn more.